I recently used Comcast aka Xfinity Wifi and saw some strange popups in the lower right hand corner caused by JavaScript injected into the page I visited because it was not over https. I read about it at arstechnica.com and pcworld.com and it seems to have started recently.
So I ask: what is Comcast doing? So I captured some code and network traffic and analyze it a bit. I captured two JavaScript files in my browser by visiting a page without https. They are posted here after running jsbeautifier on them: GitHub GIST
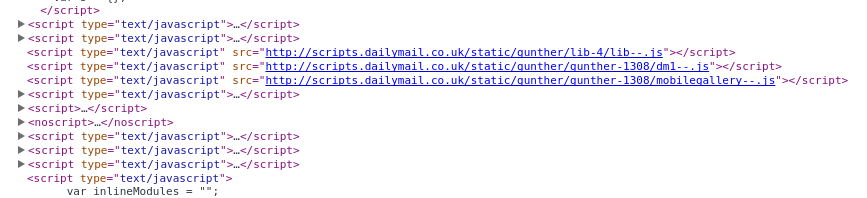
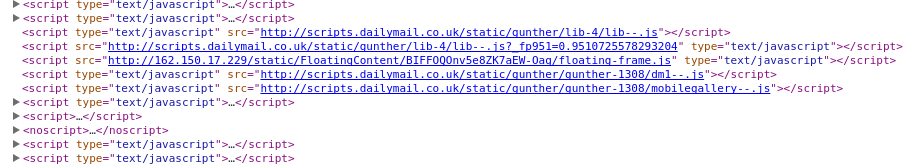
First lets talk about how they put the javascript on the page I visited. Here is how the code looks normally:
And now after the injection:
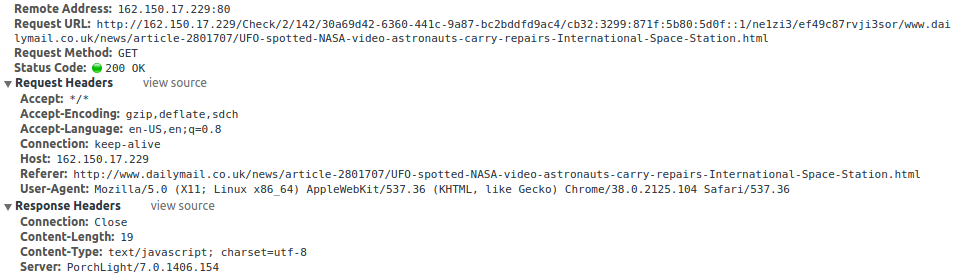
So it appears only one line was added but the other included were out of order… which would imply they parsed the entire DOM and then rendered the HTML again. What else did they extract from my page view? Studying the network traffic also shows something was sent back to Comcast with data in the GET request. there was an empty response but it states it was sent with a PorchLight/7.0.1406.154 Server which doesn’t seem to have results on Google.
So what is the code doing? One function that does not have it’s name erased is “sendAccounting” which is shown here. I think the “(f + u)” is hilarious given the context.
function sendAccounting(o, t) {
o = o || 1;
t = t || 0;
var e = new Image;
11 == t || C && 6 == t || (e.src = "http://162.150.17.229:80/" + o + "-142/30a69d42-6360-441c-9a87-bc2bddfd9ac4_cb32:3299:871f:5b80:5d0f::1/" + t + "." + (f + u));
return e
}
This code is called here:
t.json._accounting = {
stopTime: c,
sendAccounting: sendAccounting,
uri: "http://162.150.17.229/static",
check: o("%TOPURLMATCH%"),
direct: !1
}
Searching for “%TOPURLMATCH%” this code seems to be referenced on the web in a Toms Hardware post which has the IP 162.150.17.217 which is very similar to the one I am seeing 162.150.17.229. “Comcast Cable” owns these IPs and the reverse DNS is xfwfpl-nwca-03.sys.comcast.net and xfwfpl-nwca-05.sys.comcast.net. The date is this post is April 30, 2014 which means this has been going on since at least then.
Next looking at the popup code it seems to filter out two domains from this popup. Why?
pe = "*.groupon.com/* *.adobe.com/*",
It seems blocking the subnet 162.150.17.x will prevent Comcast from launching these scripts from working.
What are the potential of these scripts? Why is this bad?
A long time ago I worked on a project to demonstrate how bad JavaScript injection can be called GravityScript https://code.google.com/p/gravityscript/ which is a general version of Google Gravity. This showcases that a small line of JavaScript code can touch everything on the page. This is the same principle behind Google AdSense. A small snippet of code is inserted on the page that analyzes the content by reading the text and renders an advertisement specific to that content.
Comcast is the ISP so they already know what sites people are visiting. What this gives Comcast is the ability to track individual user’s browsing habits instead of being confused by seeing an entire household’s network traffic as one user. Beyond all the traffic Comcast can already observe JavaScript in the browser gives them the ability to see where your mouse is, what your screen resolution is, what browser you are using, and what plugins you have installed.